Video marketing revolves around the promotion of a brand and its services or products through the use of video content. Its goal is to drive sales, foster social network engagement, augment website traffic, accumulate email signups, and elevate customer service standards.
Building a strong brand presence with video marketing

Cybersecurity jargon made simple

Cybersecurity is a crucial component of managing a successful company and understanding different cybersecurity terms is essential to protecting your company's sensitive information, data, and assets can be deleted. Here’s a guide to key cybersecurity terms every business owner should know.
How technology is revolutionizing healthcare

From the widespread adoption of electronic health records for seamless data management to artificial intelligence-driven diagnostics and telehealth services, technology is empowering healthcare professionals to deliver better care and improve patient experiences.
How call recording drives business growth

Call recording software provides an efficient and cost-effective way to monitor, analyze, and optimize customer interactions. In this article, we will explore the benefits and applications of call recording, and how it can contribute to the success of your business.
Your essential guide to Microsoft Whiteboard
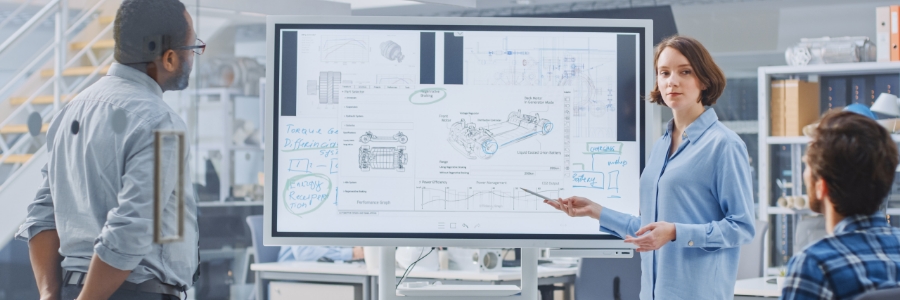
In the age of remote work and distributed teams, effective collaboration and visual communication are vital for business success. Microsoft Whiteboard serves as a digital canvas where teams can collaborate in real time, regardless of their physical location.
How to find the right cloud service model for your business

Cloud computing has become a ubiquitous part of the modern business landscape. But with so many different cloud service models available, it can be tough to determine which one is right for your business. In this article, we'll break down the different types of cloud service models and help you choose the one that's right for you.
Essential guide for mitigating data loss

Data loss can have severe consequences, including financial loss, reputational damage, and legal issues. Therefore, implementing robust measures to safeguard your business data is essential. Here are some important steps you can take to protect your business from data loss disasters.
Securing SMBs: The role of managed IT services in cybersecurity

Small- and medium-sized businesses (SMBs) face persistent cybersecurity challenges. These businesses are often targeted by cybercriminals due to their valuable data and limited security resources, but that doesn’t mean that they're helpless. Managed IT services providers (MSPs) can help SMBs strengthen their cybersecurity with comprehensive solutions and services.
How to keep your Mac safe

Many users believe that Mac laptops and desktops are more secure than Windows devices. However, Macs are still susceptible to cyberthreats, and they’re becoming more so as cybercriminals continue to search for new ways to exploit vulnerabilities in Mac devices.
